#Proactıvesoc  VIRTUAL event serıes
VIRTUAL event serıes
Improve your SIEM Log Management with
ON-DEMAND WORKSHOP
Supercharge your Security Operations Center.
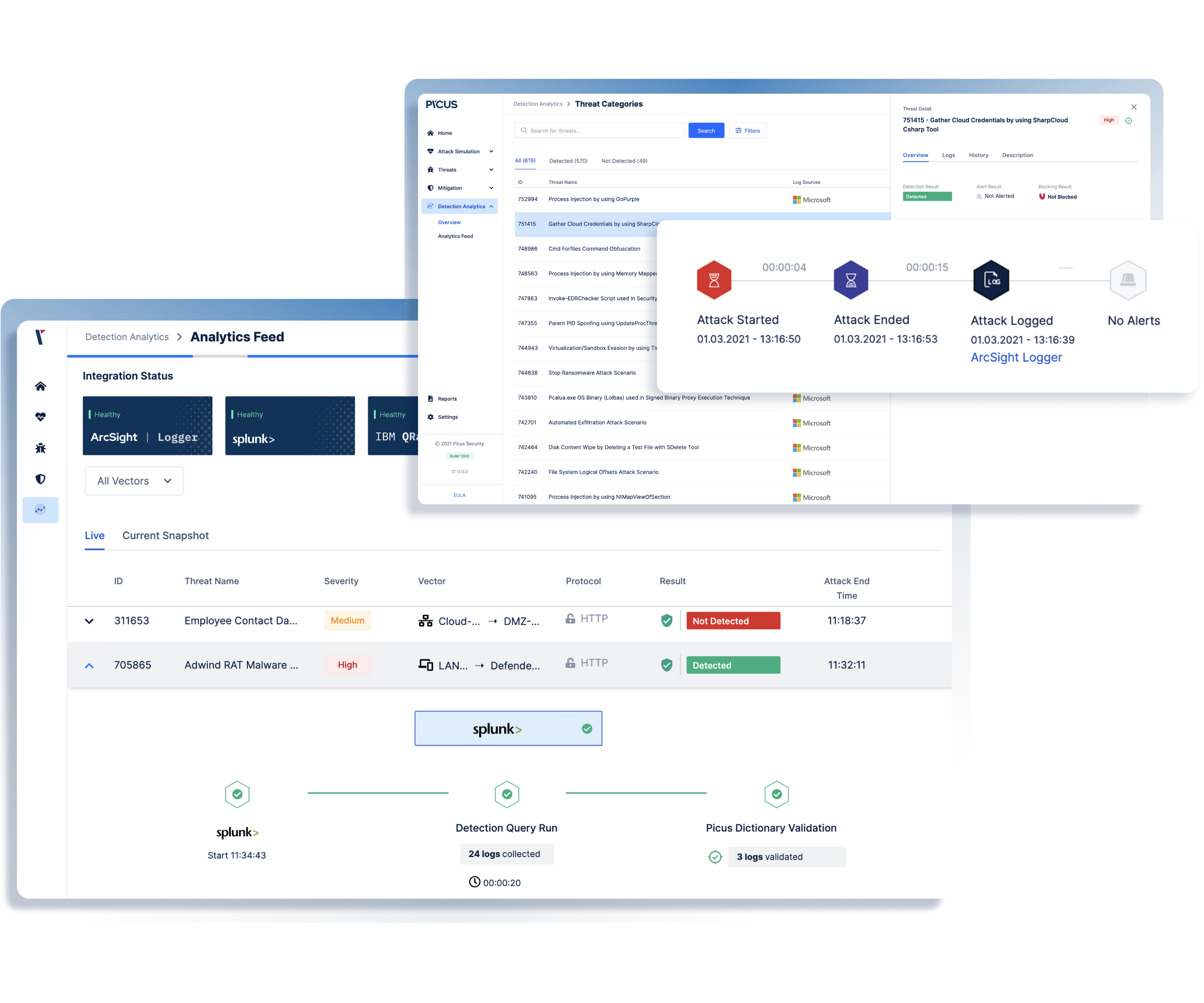
Given the complexity of the log management function, SOC practitioners have to deal with all combinations of failure involving malfunctioning log sources, invalid log format or temporary service disruption, while adapting the scope of log collection to the changing adversarial landscape.
Ishak Celikkanat, SOC Consultant at Picus Security, shows the threat-centric validation process that allows SOC teams to proactively and consciously apply log management best practices.
Topics covered in this session include:
-
How to Identify Missed Logs for Reducing Risk?
-
How to Enhance Logging for Better Visibility?
-
How to Optimize Endpoint Logging by Leveraging Threats?
-
Threat-Centric Cyber Security: Log Validation with Attack Simulation

